Have you heard the good word about Tailscale, madam?
It's the latest and greatest mesh VPN software. It's pretty cool, it's the backbone of my homelab and my public facing server infra, most of my devices connected 24/7, it solves all my networking edge cases, and it's pretty much never let me down over the >4 years of my use. I've got all my friends on it and a bunch of the cool tech blog people use it. What more could you want?
Oh, you want a long and overly verbose explanation of every use case I or someone I know has for it? Well, if you insist...
I have no professional or monetary connection to Tailscale at the time of writing. I'm literally just a user of their software and think it's this good. I think some of my friends used to work there? But I don't even really remember.
Everything Can Reach Everything - Always, Anywhere
At its core, Tailscale is a VPN, or a Virtual Private Network. Even if you've never heard of a VPN before, you've used a plain ole private network the last time you printed something or used AirPlay or connected to your wifi router to change the password. It's a network of devices with very few restrictions on connection - everything can (basically) talk to everything else. Most of the time, we run our homes and offices this way, and the security rule is "You need to be in this physical place to connect", which actually works pretty well for keeping the Russian hackers out.
However, these days this is getting less and less practical. Between remote work, the cloud, and hackers just parking a van across the street to break into your wifi, there are now many, many cases where "being in the same place" really isn't a good enough rule anymore, and that's where VPNs come in. They allow you to take this physical network privacy concept and put it on the internet, creating a virtual place where all your devices can talk to each other securely, no matter where they are.
Well, that's the dream anyway. Historically, VPNs have been a pain in the ass to get working for a boatload of reasons - requiring dedicated VPN controller servers that are on the public internet, arcane security and authentication requirements, and a user scheme based on people's identities rather than devices. For decades, it's been hard to actually get a VPN set up that works well as an individual, and if you did it would be a decent amount of work to keep up, and sometimes you just wouldn't be able to connect.
Tailscale has changed all that. Based on a relatively new and much more efficient VPN technology called WireGuard instead of the classic OpenVPN, they run direct connections between all your devices and they only handle some parts of authentication and NAT punching, without having to ever process any user data[[1]]. You just sign into your account on a device and it can now reach all your other devices, no questions asked, anywhere with internet. It doesn't slow down your internet or change where Google thinks you are or make you do a bunch of captchas, because it doesn't even affect normal internet traffic at all, only adding new connections between your personal devices.
It's fucking amazing!!
It Literally Just Works
This is the single most important thing, and the hardest thing for any VPN product to get right. Tailscale just works. I don't know how many thousands of hours it took to get the last 20% of a VPN product nailed down but yeah it's great. If I want to connect from one of my machines to another and both machines are on, Tailscale works.
It works on my laptop. It works on my phone. It works on my Apple TV. It works on my ARM64 servers and my ARM32 Raspberry Pis. It works inside a Docker container running on vast.ai. It worked in Europe and in India. It sometimes works on a plane without paying for wifi, and it's worked on an Amtrak train[[3]]. It works on my two separate Docker networking sidecar containers under some pretty crazy userland networking environments.
It just works, day in and day out, without a single outage that I've felt.
It Just Works. And that's so special these days.
Share Machines like you share Tweets
So, let's say you have a machine somewhere running something and you want your friend to be able to connect. For me, this is usually Minecraft servers, but sometimes it's a Kubernetes controller or a local webserver running a demo app on my laptop. Whatever the reason, this is usually a royal pain in the ass and a security nightmare! The usual procedure is to find your devices' local IP, make sure you change its DHCP assignment to static, port forward that on your router, find your public IP, hope that it doesn't rotate and that you're not behind a double NAT, and then finally send that IP to your friends. Oh, and you had better hope that your app is secure, because it's now on the public internet and hackers will be scraping it every few minutes for security holes[[2]].
Tailscale has changed all that. Now, all you need to do to let a friend into your device is go to tailscale.com/admin and generate a sharing link for your server. Once your friend clicks that link and accepts the invite, they can now connect to your device from wherever they are, on any device that has Tailscale. It's so, so much easier!
Ten out of my 38 machines are shared out like this in some way, and it's an amazing system that has changed how I can work with my devices.
Airdrop – Anywhere, Anytime, Any Device
If you have an apple friend, or if you are the apple friend, you might have seen Airdrop before - an absolutely killer feature of the ecosystem, where anyone can send a photo, video, or file to anyone near them. It's a real problem solver when you have a 45-minute video on your phone and no USB C cable, but it's an Apple exclusive and I have spent many hours writing tools that solve this in various other ways. Thankfully, Tailscale has us covered here too, with Taildrop.
Taildrop lets you send any file to any device on your tailnet, at any distance, securely encrypted and at pretty much the full network speed. It's pretty simple, but there's so few ways to do this well today. It's another thing that Just Works to solve otherwise stupendously frustrating problems, like getting 120GB of training data from an iPhone onto your GPU server when you left the server 600 miles away at home.
Explicit Permissions for Your Network
Having everything talk to everything on your network is pretty cool, but what if that's not what you want? What if you don't trust some machines, or run your LLC off the same server you used for Minecraft last week and shared with your friend? What if you need to let your friend access just your Plex but don't trust them around your 3D printer controller?
Then, you want Tailscale Access Control Lists (ACLs)! With these, you can define groups of both people and machines and write granular rules for access, all the way down to the port level. I use this to draw extra security boundaries around less trusted nodes, share with a finer granularity, cordon off honeypots and otherwise "targeted" machines, and to make it easier to sleep with my habit of setting raspberry pis with tailnet access in random places. Killer feature.
Infrastructure Backhaul
I'm pretty cheap. This means I really don't like paying for servers, because they're annoyingly expensive and I'm already paying a subscription for a domain and for internet, so why should I pay Azure $70.08 a month for compute when I can just put Linux on the 7-year old laptop that lives under my bed and be done with it?
Unfortunately for me, paying for Azure gives you a bit more than just the server. One such treasure is the privilege of not having people connect straight to your house! I don't remember the last time I updated my router, and those things are chronically full of security issues. To be clear, it's usually fine, but if you forget a step in that whole rigmarole I described earlier to port forward it doesn't work, and it can really be a security nightmare to keep everything safe.
You, like my parents, might also not even have a public IP you can use for your home network (the double NAT situation I mentioned earlier), or you might have one that rotates unpredictably. In any case - Tailscale provides a solution! Instead of putting our workloads in the cloud directly, we can rent the cheapest server you can find - about $5 a month in 2025 - and use it as an ingress node for our entire network. Users connect to our cloud-hosted cheap machine, then the traffic is securely forwarded to your real large computers, wherever they are!
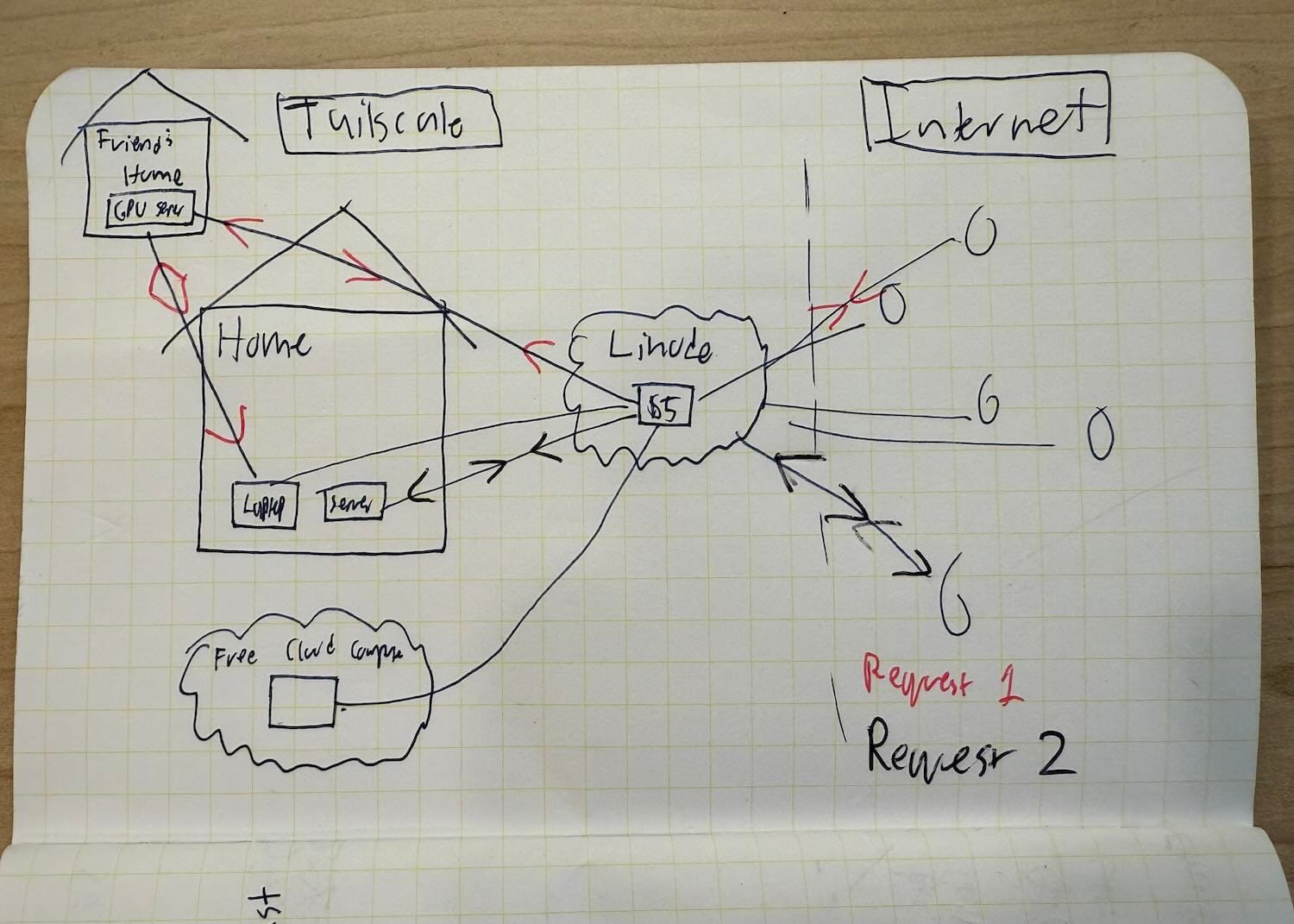
I've been running just about this exact pictured setup for the better part of four years now. It's been perfectly stable the entire time. Literally bulletproof.
They Did A Thing With DNS That Mostly Works
Tailscale gives each device a new IP address - like the one your computer gets from the router or the one your router gets from the ISP - that they all can use to reach each other. Even if you're as crazy about networking as me though, you'll never memorize all these IPs and it's really annoying to have to like bookmark every URL you'd want to use on them.
To fix this, Tailscale added Magic DNS - allowing me to just go to a URL like https://server-name:4646 to access my Nomad controller instead of having to remember the whole IP. What's really remarkable about this though is just how consistent it is! If you know much about networking, you'll know how just god damn finicky DNS is, especially when you want to do something quirky with it like this. I have no idea how they got this to be so stable across so many devices, but really kudos to them.
ngrok But Not Hounding Your For Money (yet)
Link sharing is great, but sometimes you want to put something small and simple on the public internet without that whole port forwarding thing - like if you want to make a webserver on your desktop available to your whole discord server for like 20 minutes. Classically, the tool for this is ngrok, which has served this role for many years. Recently though, they've started wanting money for this service they so kindly used to provide to the entire internet for free, which is a no-go for me (see - I Am Cheap).
Tailscale also solves this for us with Tailscale Funnel! With it, you can temporarily make a normal, publicly accessible URL you can send to anyone online, which connects to any port on any machine you have in your tailnet. It has automatic SSL termination so HTTPS just works automatically and the URL, while a little long, is still pretty damn normal. This is another one of those edge case features that you don't use every day but when you do, it solves a problem that would have been a royal PITA to solve without it.
Oh what's that, you want to do this but just with devices in your tailnet? Yeah they do that too, it's called Serve. I wish these had different names, I always get them mixed up.
Exit Nodes - It can be the other kind of VPN, too
If you're not that deep into networking, the kind of VPN you've probably heard of before is the kind like Nord VPN or Mullvad or whoever is paying for youtube ads this week. What these do is tunnel all your device's traffic somewhere else, for either faking your location to get different Netflix shows or purported privacy/security benefits like hiding your traffic from your ISP or your local government. It's extremely questionable how well this stuff works from that end for a few reasons, but I am a fan of the Netflix problem that they sometimes solve.
Thankfully, Tailscale also has this solved with Exit Nodes. Remember like five minutes ago when I said "... it doesn't even affect normal internet traffic at all"? Well, if you want it to, it can! You can mark some machines as an "Exit Node," then you can have your device send all its traffic through to that. I have a few exit nodes in the US and one at my friend's house in India, and I find them endlessly useful to solve little edge case problems all the time, from getting past a restricted wifi network to getting back to my home country's internet when I'm traveling.
Sidecar Containers - Take The Magic Anywhere
This one's even more specific than the rest, but it's incredibly helpful when you really need it. Apologies for the pile of jargon but we're going a bit deep here.
Sometimes, you want to expose a webserver running inside a Docker container. This can be challenging, as it requires either port forwarding or setting up an entire reverse proxy and service mesh stack in your environment, which is great for your "main" running environment but not always what you want to do, especially when you're running the container somewhere weird or somewhere you don't control the route out to the internet.
In this situation, you can setup a tailscale sidecar networking container in the same Docker Compose file as your main service container! They have a whole blog post about it that I really recommend you read, and they publish a Docker container that you can drop in and use. It supports automatic funnel/serve setup if you want, creating a very slick set-and-forget experience to handle ingress routing in even more edge case environments.
Sadly, this doesn't seem to yet support container sidecar egress routing through an exit node. Something to look forward to soon!
End uncontextualized jargon pile, read on for some closing thoughts!
The Future
Now, Tailscale seems to still be in the saas company golden years. Investment is still flowing in, enshittification pressures are a ways away, and there's still not much of a pressure as a user to give them money. Life's good.
It feels like we've seen this story a million times at this point, things are all peachy right up until the money stops being so free and they need to find a way to extract a profit, then everyone gets squeezed. Facebook, BeReal, Hashicorp, Redis. Ngrok, mentioned earlier, is in the middle of this process right now. A tale as old as time.
Honestly, this probably is Tailscale's future. There's some part of me that just says "get in while the water's still nice, it'll be fun for a few more years" and be done with things, but I do think they're reasonably well positioned to not get too bad in the near term.
For one thing, their costs are pretty damn low. One of their best decisions has been to keep connections peer to peer instead of hub and spoke, meaning my laptop connects to my desktop just through my wifi, without having to go through the internet to Tailscale's server and back again whenever possible. This is great for me (yay faster pings!) and great for Tailscale's budget (yay no cloud egress costs!). They've been trending away from this with some of the more recent features, including funnel which proxies internet traffic through their servers, but the core product is still pretty good on this front. This means lower costs for them and hopefully a longer runway before things start going belly up.
They're also reasonably open source, which is cool! Their client apps are open source and people are re-implementing their control plane. There are few of these projects and they're not yet at feature parity with the official hosted control plane, but they're getting closer and will probably be ready to replace it for the weirder internet-y features like funnel and taildrop and ACLs within a few more years.
On the whole, I'm so thankful for everything they've done to push forward the SOTA for VPN networking and all the utility they've added to my life! If something I mentioned here seems useful to you right now, give it a try. I really think you'll find it super useful!
[[1]]: They have other features - like funnel and serve - that do require processing user data. The core feature set of VPN connectivity between devices though is all hands-off-the-data from their end, which is both more secure for us and allows them to run everything for ~free!
[[2]]: Someday, I will publish my little bit of data from a Minecraft honeypot server I set up to track the activity of mc server scanners. Someday
[[3]]: Jesus christ Amtrak. Please fix the internet on the Pacific Surfliner